- HR Software
- Solutions
Industries
By Role
Other Solutions
- Learn
- About
- Pricing
- PeoplesHR XNew
PeoplesHR
Trust Portal
At PeoplesHR, your data security and privacy are our top priorities. We comply with global data protection regulations, using encryption, secure infrastructure, and regular third-party audits to safeguard your HR information. Our cloud-based platform ensures 24/7 monitoring, disaster recovery, and customizable access controls to give you full control over your data. With secure development practices and dedicated threat monitoring, we proactively address potential risks, providing a safe and reliable environment so you can focus on growing your business.





Overview
Information Security
At our organization, we take a comprehensive approach to information security to ensure your data is protected. Physical Security involves safeguarding our buildings and equipment from unauthorized access or damage. Cryptography is used to encrypt data, making sure that only authorized individuals can read or alter it. We follow Secure Software Development practices to create software that is built with security in mind from the start, reducing the risk of vulnerabilities. Our Security Operations team actively monitors and manages our systems to detect and respond to potential threats. Incident Management outlines how we handle any security breaches or problems, aiming to resolve them quickly and efficiently. Finally, Internal Processes Security focuses on protecting the procedures and systems we use within our organization to keep everything running smoothly and securely.
Our organization's information security is overseen by a dedicated team known as the Information Security Steering Committee. This committee includes key individuals such as the Chief Information Security Officer (CISO), Deputy Chief Information Security Officer (DCISO), Information Security Officer (ISO), and Heads of Departments. Additionally, our Compliance Manager is part of this team, ensuring that all security practices align with regulatory requirements and industry standards. Together, these professionals work to develop, implement, and monitor our information security strategies to protect our data and systems effectively.
Product Security
Enterprise Security Manager
The security of our Human Resource Information System (HRIS) is crucial for protecting sensitive employee data and maintaining operational integrity. The Enterprise Security Manager (ESM) is the primary security tool used within our HRIS product to address various security concerns
Our networked enterprise software suite greatly enhances organizational efficiency by breaking down communication barriers and streamlining processes. However, this interconnected environment also introduces potential risks, such as unauthorized access to confidential information, misuse of system commands, alteration of critical data, and exceeding granted permissions.
The PeopleHR Enterprise Security Manager is specifically designed to tackle these issues effectively. It provides comprehensive protection by safeguarding against hacking attempts, preventing unauthorized actions, and ensuring that all data and system interactions are securely managed. With the ESM in place, we ensure that our HRIS remains robust, secure, and reliable.
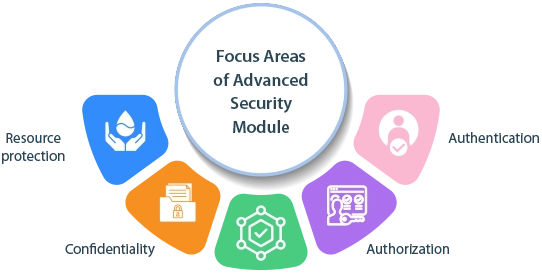
Each focus areas are equally important to cover overall objective of the advanced security module.
Ensures that only authorized users can access specific objects within a system, preventing unauthorized access.
Controls:
Controls:
- Capability Groups: Define and manage user access based on specific roles or capabilities.
- Table Base Security: Protects sensitive data in tables by controlling access at a granular level.
Verifies the identity of users to ensure they are who they claim to be. Authenticated users are granted permissions based on their authorization levels.
Controls:
Controls:
- Basic Authentication: Requires users to provide a username and password.
- Multi-Factor Authentication (MFA): Enhances security by requiring multiple forms of verification.
- Single Sign-On (SSO): Allows users to access multiple applications with one set of login credentials.
- Bio Metrics
Determines if an authenticated user has permission to perform specific actions or access certain resources within a system. Authorization is typically based on the user's identity and their authenticated status.
Controls:
Controls:
- Security Groups: Define and manage permissions for different user groups to ensure appropriate access to resources.
Ensures that data and systems maintain accuracy and consistency. Data integrity guarantees that information is protected from unauthorized changes, while system integrity ensures that the system performs as expected.
Controls:
Controls:
- Audit Logs: Track and record changes to data and system activities to verify integrity and detect unauthorized alterations.
Ensures that sensitive information remains private and is only accessible to authorized individuals.
Controls:
Controls:
- Table Encryption: Encrypts data stored in tables to protect it from unauthorized access and ensure confidentiality
Cloud Security
In our approach to Cloud Security, we focus on several critical areas to ensure the safety and reliability of our cloud-based services. Cloud Infrastructure Security involves protecting the underlying hardware and software components of our cloud environment from unauthorized access and vulnerabilities. We also have robust Backup Contingency plans in place to ensure that data is regularly backed up and can be quickly restored if needed. Additionally, our Disaster Recovery procedures are designed to help us swiftly recover from any major disruptions or failures, minimizing downtime and ensuring continuity of service.
Our product is based on a Software as a Service (SaaS) cloud model. This means that our users access and use the software application directly over the internet, rather than installing it on their local devices or servers. With the SaaS model, all updates, maintenance, and management of the software are handled on our end, ensuring that users always have access to the latest features and improvements without any hassle. This approach provides convenience, scalability, and reliable performance, allowing our users to focus on their work while we take care of the technical details.
| Feature | Description | Shared Cloud | Dedicated VMs | Dedicated Cloud | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Infrastructure Availability | Guaranteed minimum infrastructure availability | 99.50% | 99.50% | 99.50% | |||||||||||||||
| Database Backup | Database backups for individual clients are maintained in accordance with the following standard backup and retention policy.
| Yes | Yes | Yes | |||||||||||||||
| Disaster recovery - Azure | The Disaster Recovery solution replicates all production workloads in near real-time from the primary site to a geographically separate DR site. In the event of an outage at the primary site, workloads fail over to the secondary location. Once the primary site is restored, the workloads will revert back to it. | Yes | Yes | Yes | |||||||||||||||
| Disaster recovery - Huawei | The Disaster Recovery solution backs up all production virtual machines to a geographically separate site every 24 hours. In the event of an outage at the primary site, the respective VMs will be brought up using the backup at the DR site. Once the primary site is restored, the workloads will revert back to it | Yes | Yes | Yes | |||||||||||||||
| Recovery time objectives (RTO) - Azure | RTO is the duration of time in which the infrastructure is restored after a disaster | 45 min | 45 min | 45 min | |||||||||||||||
| Recovery time objectives (RTO) - Huawei | RTO is the duration of time in which the infrastructure is restored after a disaster | Best effort | Best effort | Best effort | |||||||||||||||
| Recovery point objectives (RPO) - Azure | RPO is the maximum acceptable amount of data loss after an unplanned data-loss incident, expressed as an amount of time | 15 min | 15 min | 15 min | |||||||||||||||
| Recovery point objectives (RPO) - Huawei | RPO is the maximum acceptable amount of data loss after an unplanned data-loss incident, expressed as an amount of time | 24 hours | 24 hours | 24 hours | |||||||||||||||
| Network Security Group (NSG) | Filters network traffic to and from Azure resources in an Azure virtual network. | Yes | Yes | Yes | |||||||||||||||
| Site to Site VPN | A permanent connection designed to function as an encrypted link between HBS and Azure cloud VN. | Yes | Yes | Yes | |||||||||||||||
| Cloud Monitor | Azure Monitor helps us maximize the availability and performance of our application | Yes | Yes | Yes | |||||||||||||||
| Defender for Cloud |
| Yes | Yes | Yes |
FAQ
Information Security
Security Accreditations
hSenidBiz accredited with ISO/IEC 27001:2022 for Information Security Management and ISO/IEC 27017:2015 for Cloud Security.
Security Governance
Comprehensive framework in place to oversee our security strategy, which includes policies, procedures, and accountability structures. The Information Security Policy covers the followings:
- Asset Management
- Human Resources Security
- Physical and Environmental Security
- Operations Security Management
- Cryptography
- Access Control
- Communications Security Management
- System Acquisiton, Development and Maintenance
- Supplier Relationships Management
- Information Security Incident Management
- Business Continuity Management
- Internet and Social Media Policy
- Cloud Security
- Compliance
You may request the Information Security Policy subjected to a NDA.
Risk Management
We adhere to a comprehensive risk management process that involves identifying, assessing, and mitigating security risks in line with ISO 27001 and ISO 27017 guidelines. Our Risk Registers are updated as necessary and reviewed annually, with both internal and external audits conducted to ensure compliance with ISO 27001 and 27017 standards
Incident Response Plan
We have a structured Incident Response Plan, outlined in our Information Security Policy, to manage security incidents effectively.
Security Incidents can be logged in the Helpdesk or through an email to infoseccompliance@peopleshr.com
Employee Training
All employees are required to complete an onboarding course focused on security. We conduct annual evaluations and host an Annual Awareness Month to reinforce security best practices.
Access Control Policies
We enforce strict access control policies, including a password policy with a minimum of 12 characters and enforced complexity. Access is granted based on the principle of least privilege, with periodic reviews conducted quarterly. Multi-Factor Authentication is also enforced, and Single Sign-On is available for internal systems.
Security Audits and Reviews
Internal security audits are annually conducted by our Internal Audit Team. External audits are performed annually by a selected audit party.
Supplier Security Reviews
Supplier evaluations are conducted during onboarding, with annual evaluations for existing vendors.
HR Security Reviews
Employees undergo thorough vetting before onboarding, and all employees sign NDAs and the Code of Conduct.
Business Continuity and Disaster Recovery
We have a Business Continuity Plan (BCP) that can be shared externally. Annual Disaster Recovery tests are conducted.
Vulnerability and Patch Management
We have a defined process for managing vulnerabilities and applying patches, detailed in our Information Security Policy. Internal systems are assessed annually or as needed, and servers are hardened according to CIS Benchmarks.
Physical Security
We have implemented stringent physical security measures to protect our assets and data. These include controlled access to facilities, surveillance systems, security personnel, and secure disposal procedures for sensitive materials. Additionally, our physical security controls are aligned with ISO 27001 and ISO 27017 standards to ensure a secure environment.
Intellectual Property
Our company protects its intellectual property through a combination of legal, technical, and organizational measures. We implement strict access controls, data encryption, and regular monitoring to prevent unauthorized access or disclosure. Additionally, our policies are designed to ensure that all employees and partners understand their responsibilities in safeguarding intellectual property, and we enforce these through legal agreements and ongoing training. Our approach aligns with industry standards, including ISO 27001, to ensure comprehensive protection
Change Management Process
Either service related or organizational related changes follow through a change management process. The process is initiated upon the requirement, or an update. Then the change is subjected to approval process and once permission granted the change is made to effect.
A changelog is maintained by system owners. If the change is related to a project, the assigned project manager maintains the change management log.
Product Security
Secure Development Lifecycle
Our company integrates security practices throughout the software development lifecycle (SDLC) by embedding security controls at every phase. This includes secure coding practices, threat modeling, regular code reviews, and vulnerability assessments. We also conduct automated security testing during development and continuous integration processes. Security training is provided to all development teams to ensure they are aware of the latest threats and best practices. By following the DevSecOps approach, we ensure that security is a fundamental aspect of our development process, aligned with industry standards such as ISO 27001 and ISO 27017.
Environment Segregation
We manage independent environments for Development, Quality Assurance, and Production, ensuring clear separation and security at each stage. Tests are conducted using simulated data, which is thoroughly sanitized before deployment to prevent any sensitive information from being exposed. This approach minimizes risks and maintains the integrity of our production environment.
Code Reviews
Code reviews are conducted regularly, and we utilize Static Code Analysis tools to ensure the security and quality of our code.
Security Testing
We conduct Security Testing on our applications and ensure they are tested for OWASP Top 10 vulnerabilities.
Vulnerability Management
Vulnerability Assessment and Penetration Testing (VAPT) are conducted annually. VAPT reports can be shared with external parties only under a Non-Disclosure Agreement (NDA). Identified vulnerabilities are addressed according to the Service Level Agreements (SLAs) of HBS.
Vulnerability Assessment and Penetration Testing Reports can be provided subjected to a NDA.
Encryption and Data Protection
We implement encryption both in transit and at rest. Data in transit is secured using HTTPS with the latest TLS 1.2 protocol, while data at rest is encrypted with the AES 256 Encryption Algorithm.
Authentication and Authorization
We have a robust authentication and authorization mechanism, including a Role-Based Access Control (RBAC) system. The application supports various authentication methods, including Basic Authentication (Username, Password), Multi-Factor Authentication (Username, Password + SMS/email), Single Sign-On (SSO) with providers like Azure and AWS, and Biometric Authentication for mobile applications.
Cloud Security
Cloud Configuration Management
Our cloud servers are hardened according to the CIS Level 1 and Level 2 Benchmarks. These controls are reviewed annually or as needed to prevent misconfigurations and adhere to best practices.
Data Security in Cloud
We enforce strict access controls aligned with our Information Security Policy (ISP). Server access is provided to the support and implementation teams through a request and approval process. Employees access servers via VPN solutions. Data in transit is secured with HTTPS using the latest TLS 1.2 protocol, and data at rest is encrypted with the AES 256 Encryption Algorithm.
Cloud Security Monitoring
We use a Security Incident and Event Management (SIEM) tool for continuous monitoring of security threats. Additionally, a Cloud Security Posture Management (CSPM) tool is used to track and maintain the overall cloud security posture, alongside continuous infrastructure performance monitoring.
Compliance with Cloud Security Standards
Yes, we are aligned with the ISO 27017:2015 cloud security controls to ensure compliance with established standards and best practices.
Backup Process
We have a systematic backup process in place, which includes full backups. The backup schedule is detailed in our SaaS Schedule to ensure data can be restored in case of loss, corruption, or other issues.
Recovery Point Objective (RPO)
The RPO, which defines the maximum acceptable data loss time, varies based on the Cloud Service Provider. For Azure, the RPO is set at 15 minutes.
Recovery Time Objective (RTO)
The RTO, which specifies the time required to recover and resume normal operations after an incident, also varies by Cloud Service Provider. For Azure, the RTO is less than 45 minutes.
Data Security
Data Security Compliances
- Personal data protection act no: 09 of 2022
- Kenya Data Protection Act
- Phillipines Data Protection Act
Data Security Policy
- Lawful, fair and transparent
- Limited for its purpose
- Data minimization
- Up-to-date
- Retention
- Integrity and confidentiality
- Consent: Where hSenid holds recent, clear, explicit, and defined consent for the client’s data to be processed for a specific purpose.
- Contract: Where the processing is necessary to fulfil or prepare a contract for the client (for which purpose hSenid would generally execute a Nondisclosure Agreement with the client)
- Legal Obligation: Where hSenid has a legal obligation to process the data determined by the contract.
- Vital Interests: Where methods of processing the data is necessary to protect the client’s sensitive data.
- Ethical Publicity: Where prior consent is sought from the data owner with respect to use of information for publicity, business development or any other activity resulting in data being exposed to the public
Special Categories of Personal Data
Data about a client that is more sensitive, due to which it requires added protection. This type of data could create higher significant risks to a person’s fundamental rights and freedoms, for example by putting them at risk of discrimination.
- Dependent data
- Emergency data
- Qualifications
- Bank details
- Passport details
- Attachments
- Permanent Address
- Contact address
- Date of birth
- NIC & Issue date
- Race
- Nationality
- Blood Group
- Civil Status
- Gender
- Married date
- Divorced date
- Details of compensation
- Any User Defined Function (UDF marked as Privacy Data)
Data Security in Cloud
We enforce strict access controls aligned with our Information Security Policy (ISP). Server access is provided to the support and implementation teams through a request and approval process. Employees access servers via VPN solutions. Data in transit is secured with HTTPS using the latest TLS 1.2 protocol, and data at rest is encrypted with the AES 256 Encryption Algorithm.
These Q&A entries will help users of your trust portal understand the security measures and policies related to cloud services, while also providing clarity on the processes and standards your company adheres to.
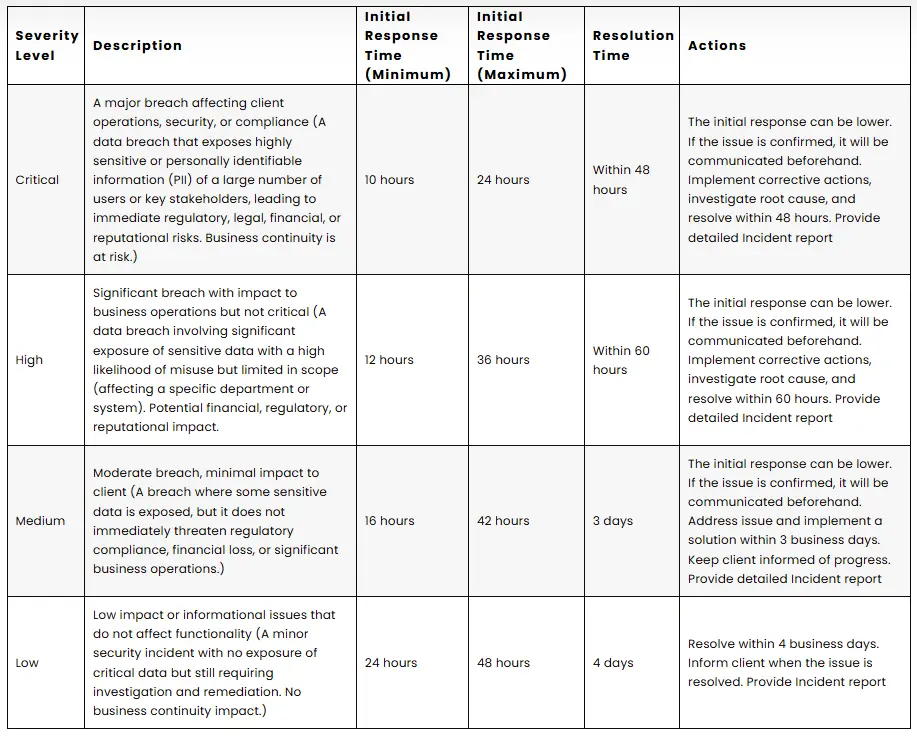
When Indicators of Data Breach is detected, an incident management procedure will be initiated.
| Severity Level | Description | Initial Response Time (Minimum) | Initial Response Time (Maximum) | Resolution Time | Actions |
|---|---|---|---|---|---|
| Critical | A major breach affecting client operations, security, or compliance (A data breach that exposes highly sensitive or personally identifiable information (PII) of a large number of users or key stakeholders, leading to immediate regulatory, legal, financial, or reputational risks. Business continuity is at risk.) | 10 hours | 24 hours | Within 48 hours | The initial response can be lower. If the issue is confirmed, it will be communicated beforehand. Implement corrective actions, investigate root cause, and resolve within 48 hours. Provide detailed Incident report |
| High | Significant breach with impact to business operations but not critical (A data breach involving significant exposure of sensitive data with a high likelihood of misuse but limited in scope (affecting a specific department or system). Potential financial, regulatory, or reputational impact. | 12 hours | 36 hours | Within 60 hours | The initial response can be lower. If the issue is confirmed, it will be communicated beforehand. Implement corrective actions, investigate root cause, and resolve within 60 hours. Provide detailed Incident report |
| Medium | Moderate breach, minimal impact to client (A breach where some sensitive data is exposed, but it does not immediately threaten regulatory compliance, financial loss, or significant business operations.) | 16 hours | 42 hours | 3 days | The initial response can be lower. If the issue is confirmed, it will be communicated beforehand. Address issue and implement a solution within 3 business days. Keep client informed of progress. Provide detailed Incident report |
| Low | Low impact or informational issues that do not affect functionality (A minor security incident with no exposure of critical data but still requiring investigation and remediation. No business continuity impact.) | 24 hours | 48 hours | 4 days | Resolve within 4 business days. Inform client when the issue is resolved. Provide Incident report |
The Data Protection Officer will formally communicate via an email during a data breach.
📁Documents
Documents

CSP SOC Reports 2023
Azure + Dynamics 365
Public & Government - SOC Bridge Letter (October – December 2023)
CSP SOC Reports 2023
Azure + Dynamics 365 + Online Services
Public & Government - SOC 1 Type II Report (04-01-2022 to 03-31-2023) 1
CSP SOC Reports 2023
Azure + Dynamics 365 + Online Services
Public & Government - SOC Bridge Letter (April - June 2023) 1
CSP SOC Reports 2023
Azure + Dynamics 365 + Online Services
Public & Government - SOC Bridge Letter (July - September 2023) 1
Our Achievements
Significant milestones and awards that showcase our growth and success over the years.
hSenidBiz first to get ISO 27017 certification from Bureau Veritas for Cloud Security Control

Winning the ISV Partner of the Year
Winning the ISV Partner of the Year for Sri Lanka and Maldives once again! Securing this prestigious award for the third time is a testament to our enduring commitment to innovation and collaboration.





























